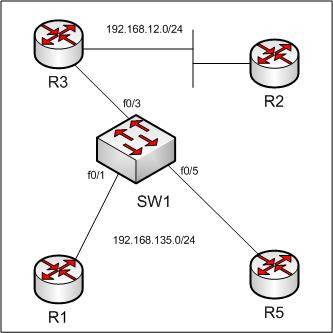
R2 is the RP and will be sending multicast pings.
R3 is the PIM DR for the 192.168.135.0 segment.
We will prevent R5 from joining group 239.0.0.1.
To deny IGMP joins on a switch, we use the IGMP filter and profile commands.
First, create the profile:
SW1(config)#ip igmp profile 1
SW1(config-igmp-profile)#deny
SW1(config-igmp-profile)#range 239.0.0.1 239.0.0.5
SW1(config-igmp-profile)#exit
Then attach it to the port:
SW1(config)#int f0/5
SW1(config-if)#ip igmp filter 1
Now we can test by having R1 and R5 join a group in the range 239.0.0.1 - 239.0.0.5
R1(config)#int e0/0
R1(config-if)#ip igmp join-group 239.0.0.1
R5(config)#int e0/0
R5(config-if)#ip igmp join-group 239.0.0.1
Let's debug on SW1 and see what happens:
SW1#debug ip igmp filter
event debugging is on
SW1#
03:26:30: IGMPFILTER: igmp_filter_process_pkt(): checking group 239.0.0.1 from Fa0/5: deny
03:26:31: IGMPFILTER: igmp_filter_process_pkt() checking group from Fa0/3 : no profile attached
03:26:33: IGMPFILTER: igmp_filter_process_pkt() checking group from Fa0/1 : no profile attached
No let's check R3 for any joined groups:
R3#show ip igmp groups
IGMP Connected Group Membership
Group Address Interface Uptime Expires Last Reporter
239.0.0.1 Ethernet0/0 00:09:28 00:02:30 192.168.135.1
224.0.1.40 Ethernet0/1 00:29:57 00:02:09 192.168.23.2
224.0.1.40 Ethernet0/0 00:30:01 00:02:37 192.168.135.3
Just to make sure, we can verify that only R1 responds to pings:
R2#ping 239.0.0.1
Type escape sequence to abort.
Sending 1, 100-byte ICMP Echos to 239.0.0.1, timeout is 2 seconds:
Reply to request 0 from 192.168.135.1, 8 ms
R2#



consise and helpfull,
ReplyDeletethanks
Brilliant LAB - thanks
ReplyDeletethank you!
ReplyDelete